When it comes to managing data these days it can definitely get a little crazy, there are just so many ways data moves around on different devices in different apps. Keeping a close eye on everything can be tricky, but one thing to help out here is Windows Information Protection (WIP). Previously known as enterprise data protection (EDP), windows information protection can help you protect against data leakage without disrupting employee workflows.
You can read more about it in the docs article.
In this blog I’m going to focus on Office 365, Teams and OneDrive since they’re closely intertwined and you’ll see why later.
Okay so let’s get started, from the Intune portal, head over to Client Apps. Here we’ll select “App protection policies” and then “Create Policy”
Go ahead and give it a name, select the platform and enrollment state.
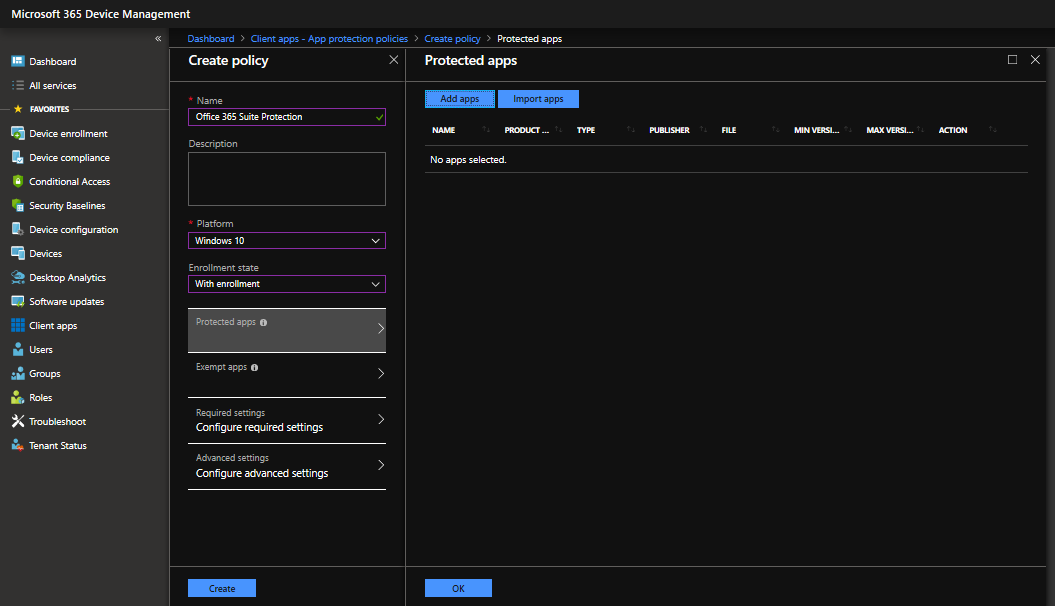
One note if you choose without enrollment:
![]()
Before we get to Protected apps, let’s talk about AppLocker real quick. In short, AppLocker consists of application control policies that helps you control which apps and files users can run. In this case, Microsoft has pre-canned Applocker.xml file for the Office 365 suite that define the allowed and exempt apps for us.
Navigate here to grab the latest policies – https://docs.microsoft.com/en-us/windows/security/information-protection/windows-information-protection/enlightened-microsoft-apps-and-wip
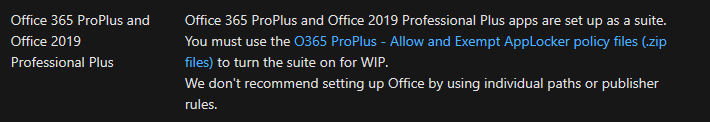
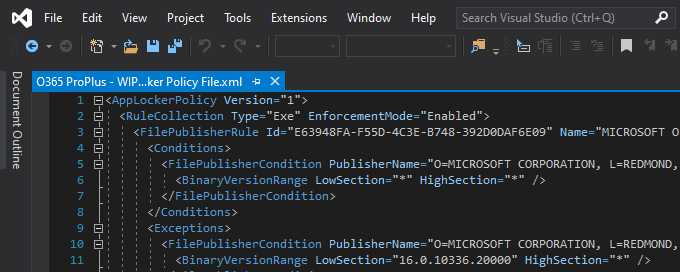
Scroll down until you see the below Product Name. Click the blew hyperlink for “O365 ProPlus – Allow and Exempt AppLocker policy files (.zip files)”
Save them.
Extract them.
Now…you may be wondering, why didn’t I just use the ones that are already there and built in?
Mostly because I thought it was good information to know : ) Hah! Not just that but it helps you understand the process of uploading new AppLocker policy files should you go down that rabbit hole someday, not to mention if you wanted to edit them.
Any who, carrying on…
For each the Protected and Exempt apps, we’ll rinse and repeat here.
(If you skip ahead, you’ll see that we end up adding OneDrive and Teams to the protected apps, so feel free to just add them now to avoid some issues that we’ll remediate)
Choose “Import apps”
Click the blue folder to upload.
Select the “Allow” version first, then so the same for Exempt”
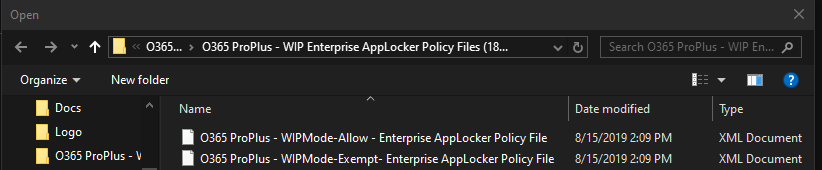
In case you’re wondering why it has 1810 in the title for the built in one, that is just the last update version. If you open the “README” that comes with the download you’ll see that’s the case.
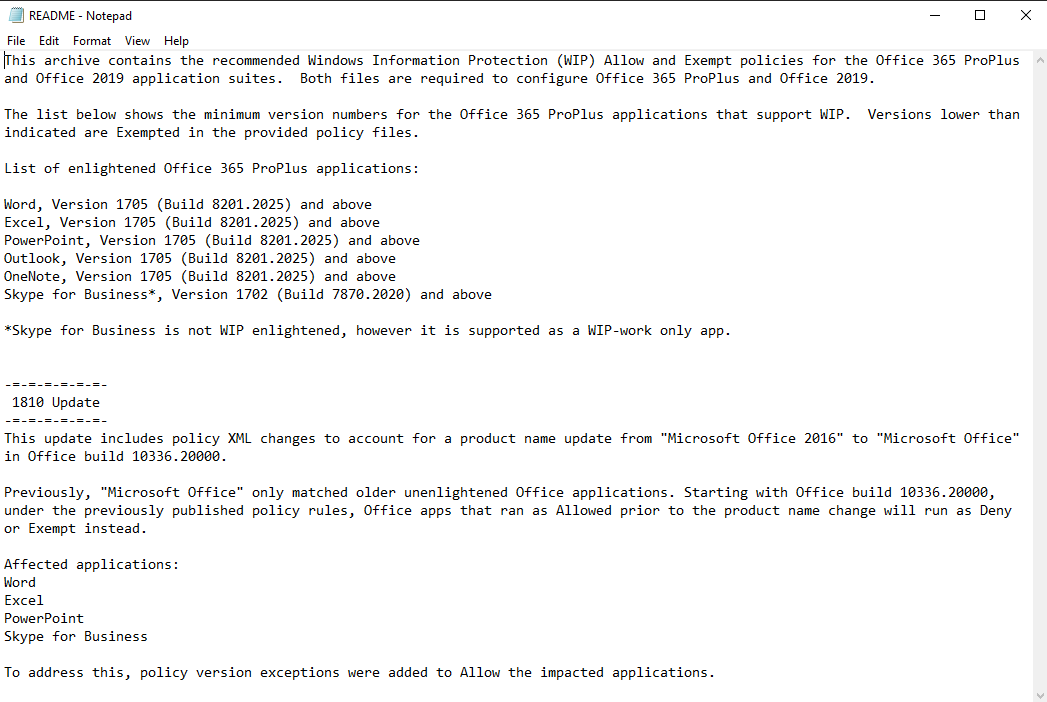
For Required settings, we have the following options for how WIP gets enforced.

I’m going with “Allow Overrides” so that I can show the behavior without breaking any workflows.
We’ll come back to “Advanced settings” a little bit later, so for now let’s just hit okay and Create the Policy.
With the Policy created, let’s go ahead and assign it.
To speed things up, I’m going to manually sync my device from Settings > Accounts > Access work or school
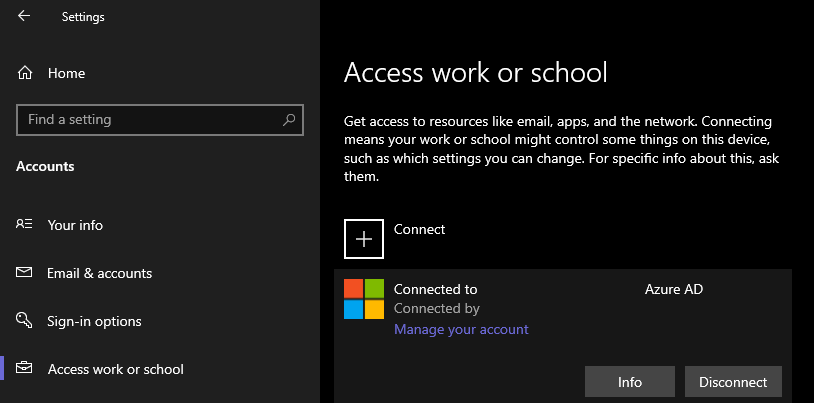
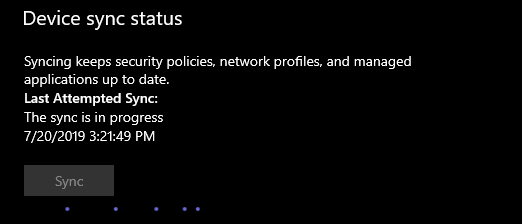
Now the first thing we’ll notice is OneDrive is “updating files”, when realistically it’s in panic mode because of its ties to the Office 365 apps which is why I said earlier we’d address OneDrive and Teams. Then a few minutes later we can see Teams having a hard time as well.
![]()
What we need to do is go back to the app protection policy that we created, go into protected apps, and add Microsoft Teams and Microsoft OneDrive like such.
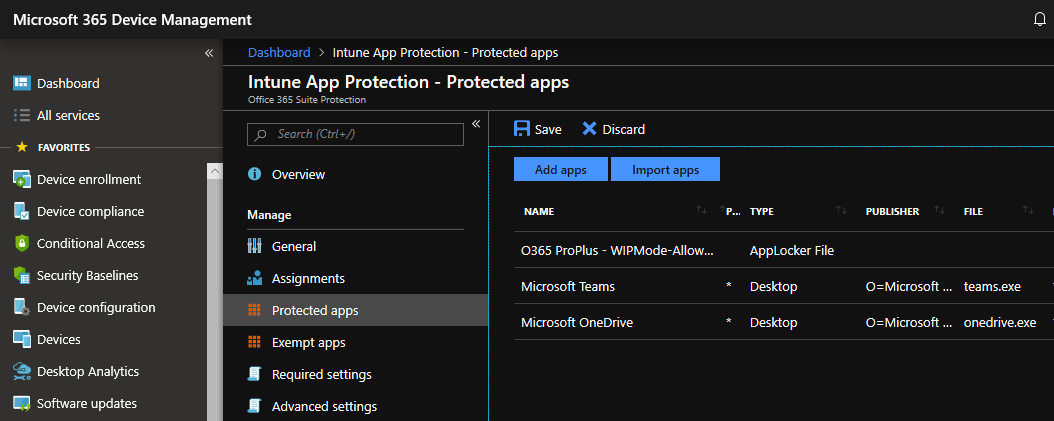
Go ahead and run another sync and those two apps will start to recover.
Teams might want to restart during this, best case it’ll hang in there until OneDrive is done processing the changes.
Eventually after a few minutes, Teams and OneDrive will be just fine again.
So now that we have our WIP policies in place, how can we tell?
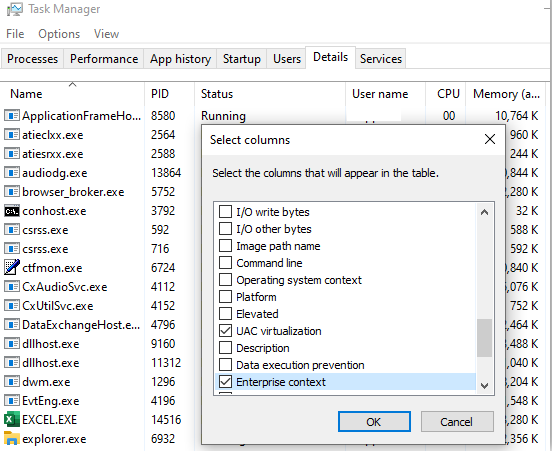
One way is to open Task Manager and choose the “Details” tab, right click on a column and choose “Select Columns”. Scroll down and check “Enterprise Context”.
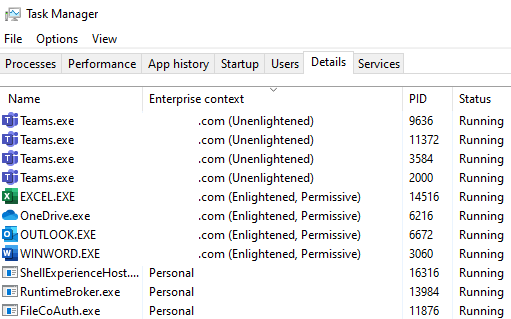
You’ll see when sorting by Enterprise context, that your domain and either (Unenlightened) or (Enlightened, Permissive) will show up. Those are the apps within your WIP policies!
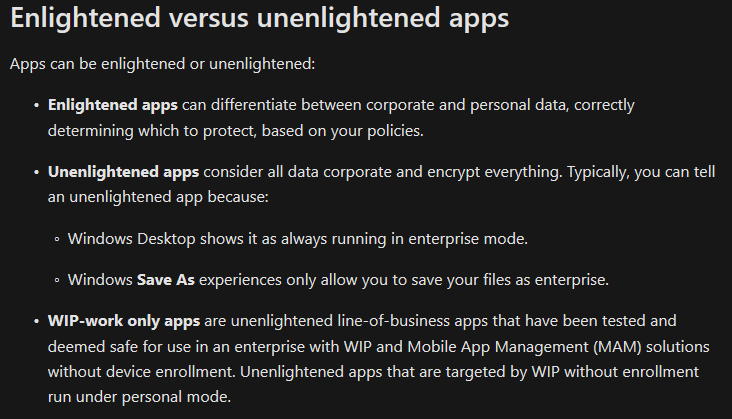
Now, how else can we tell? Let’s head back to our WIP policy in Intune. Go into the advanced settings and turn on the “Show the enterprise data protection icon”
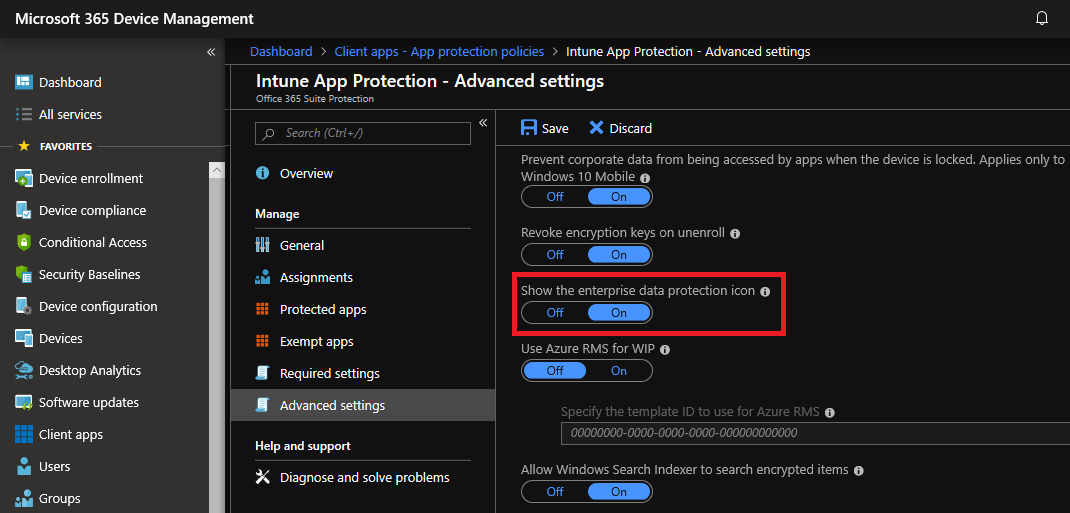
Once that’s enabled, you’ll see the brief case on the Teams app and icons on your OneDrive folders.

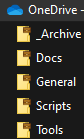
Some examples of this protection:
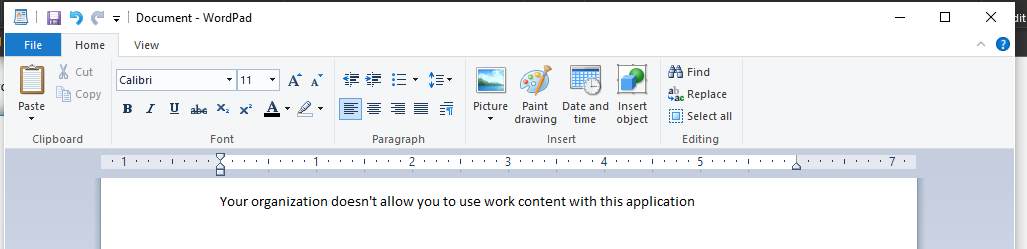
If I try copying information out of Teams or any Office program and paste into a non WIP protected application, I’ll see the following:
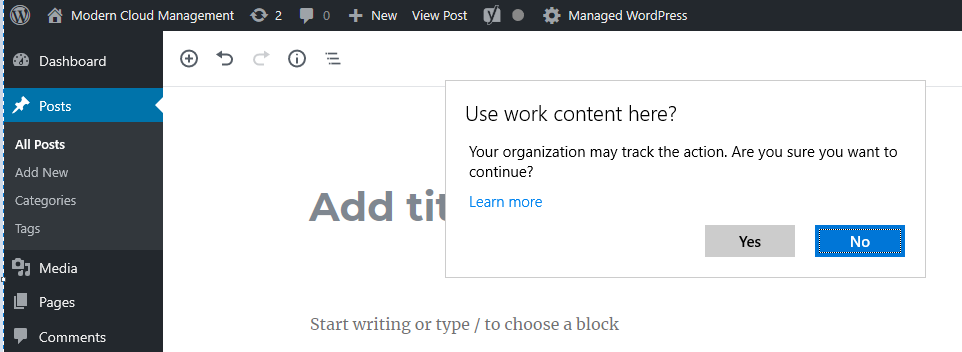
Trying to upload content to a browser, so this could be personal email or simply trying to upload corporate content where you shouldn’t.
And that’s it!
I have another blog half written that will go into the weeds a bit as well as the Auditing side of this so look out for that. I’d love to hear any questions, comments or corrections.
Thanks