This article will cover the process of addressing the Spectre and Meltdown vulnerability using Configuration Manager for Task Sequence deployment coupled with a Configuration Baseline for compliance reporting.
Contents
Step 1 – Import & Deploy Configuration Baseline
Step 2 – Package and Deploy the registry keys and Meltdown-Spectre patches via Task Sequence
Step 3 – Deploy firmware update (Add to Task Sequence – Optional)
Step 4 – Understanding levels of protection
Firmware vendor list
Article Sources
Step 1 – Import & Deploy Configuration Baseline
The official baseline release can be found here.
Starting in the SCCM console, Assets and Compliance > Compliance Settings > Configuration Baselines
 Choose Import Configuration Data:
Choose Import Configuration Data:
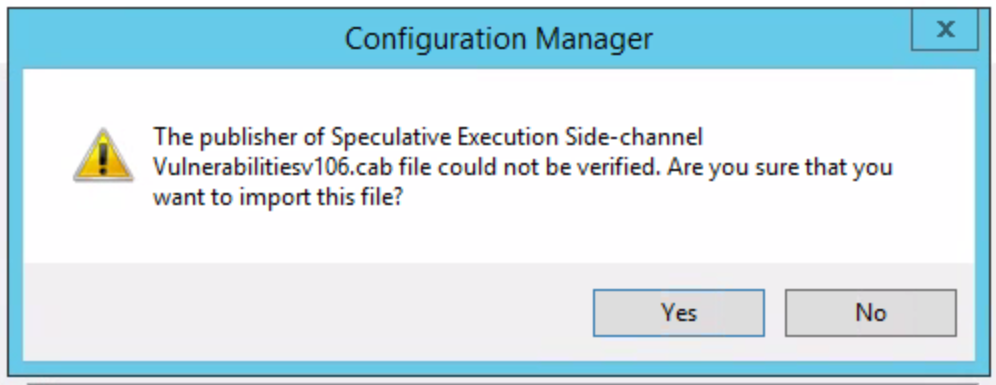
 Click “Add” and choose the “Speculative Execution Side-channel Vulnerabilitiesv106.cab” downloaded from the link provided in the article above. You’ll notice the following error, assuming that’s ok with you, choose “Yes” and continue.
Click “Add” and choose the “Speculative Execution Side-channel Vulnerabilitiesv106.cab” downloaded from the link provided in the article above. You’ll notice the following error, assuming that’s ok with you, choose “Yes” and continue.
 Once added, choose “Next” and you’ll see the following, click “Next” and continue:
Once added, choose “Next” and you’ll see the following, click “Next” and continue:
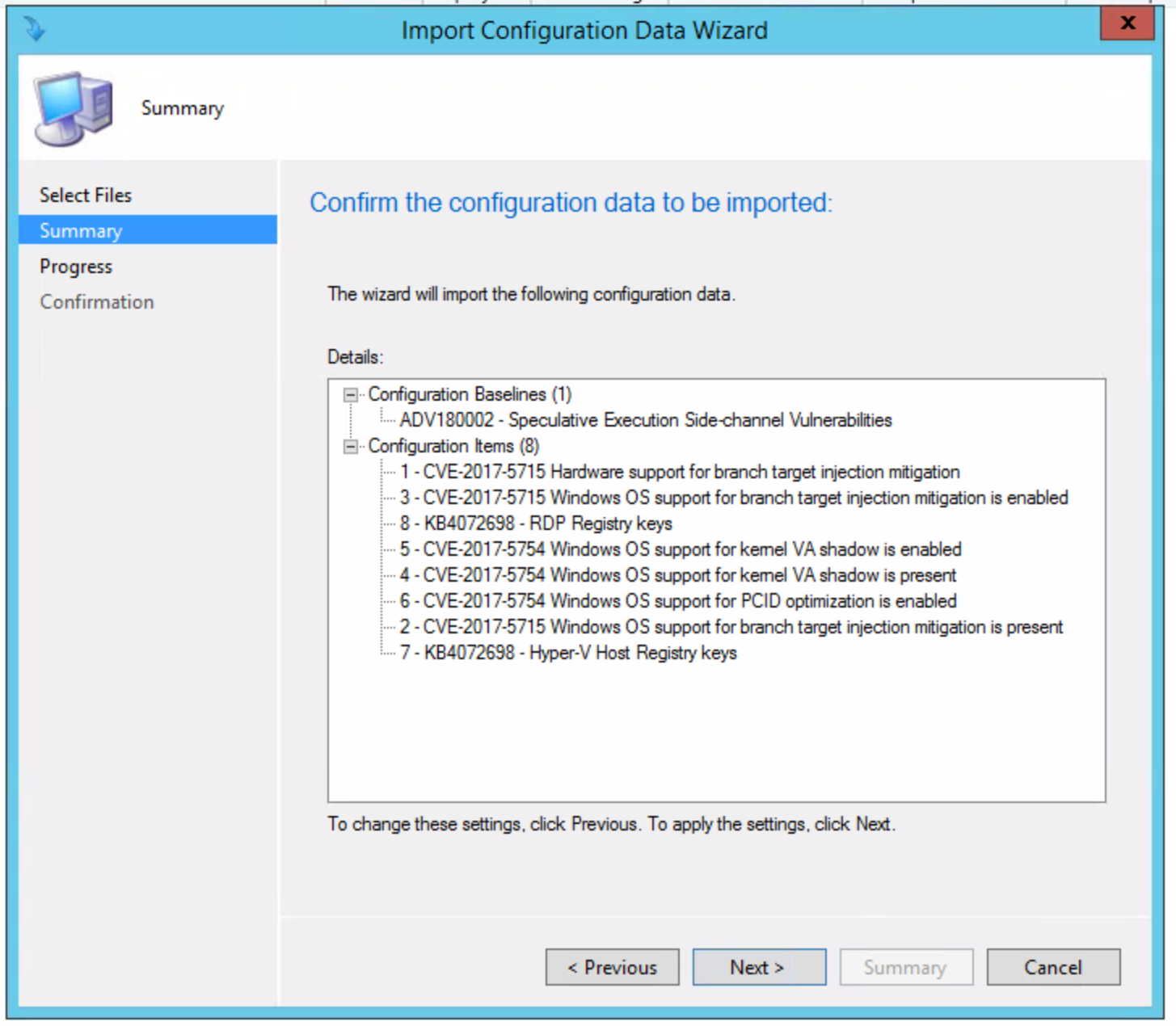 Once complete, you’ll see the following:
Once complete, you’ll see the following:
 Close the Import Configuration Data Wizard once it finishes. You’ll now see the following under Configuration Baselines in the folder where you Imported it.
Close the Import Configuration Data Wizard once it finishes. You’ll now see the following under Configuration Baselines in the folder where you Imported it.
 Since we are testing this first, I went ahead and created a test collection where I will deploy the Configuration Baseline. *Please test before you deploy to production*
Since we are testing this first, I went ahead and created a test collection where I will deploy the Configuration Baseline. *Please test before you deploy to production*
 Now that we have the Configuration Baseline added, our test collection created, we can deploy the Baseline. Head back to Assets and Compliance > Compliance Settings > Configuration Baselines, right click on the newly created Baseline and choose “Deploy”. Or choose from the ribbon.
Now that we have the Configuration Baseline added, our test collection created, we can deploy the Baseline. Head back to Assets and Compliance > Compliance Settings > Configuration Baselines, right click on the newly created Baseline and choose “Deploy”. Or choose from the ribbon.
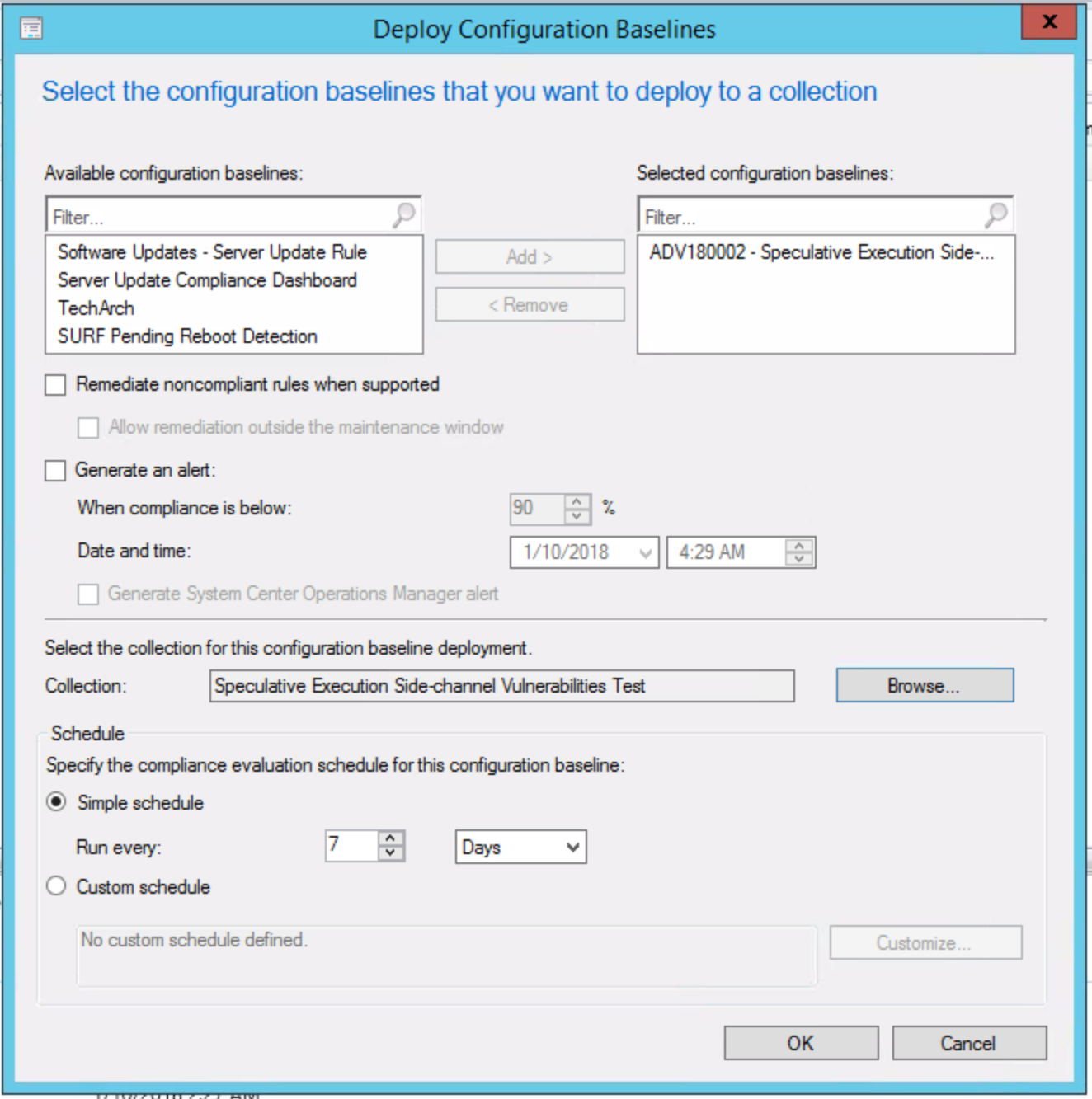 From deployment wizard, we have the option to check “Remediate noncompliant rules when supported” which will automatically remediate the registry entries, however, we will opt to deploy the registry changes via a task sequence and use this baseline for reporting only. Choosing this would automate the remediation within your maintenance windows, otherwise checking “Allow remediation outside the maintenance window” would allow for remediation sooner.
From deployment wizard, we have the option to check “Remediate noncompliant rules when supported” which will automatically remediate the registry entries, however, we will opt to deploy the registry changes via a task sequence and use this baseline for reporting only. Choosing this would automate the remediation within your maintenance windows, otherwise checking “Allow remediation outside the maintenance window” would allow for remediation sooner.
We should see the following on the deployments tab once the Baseline is deployed:
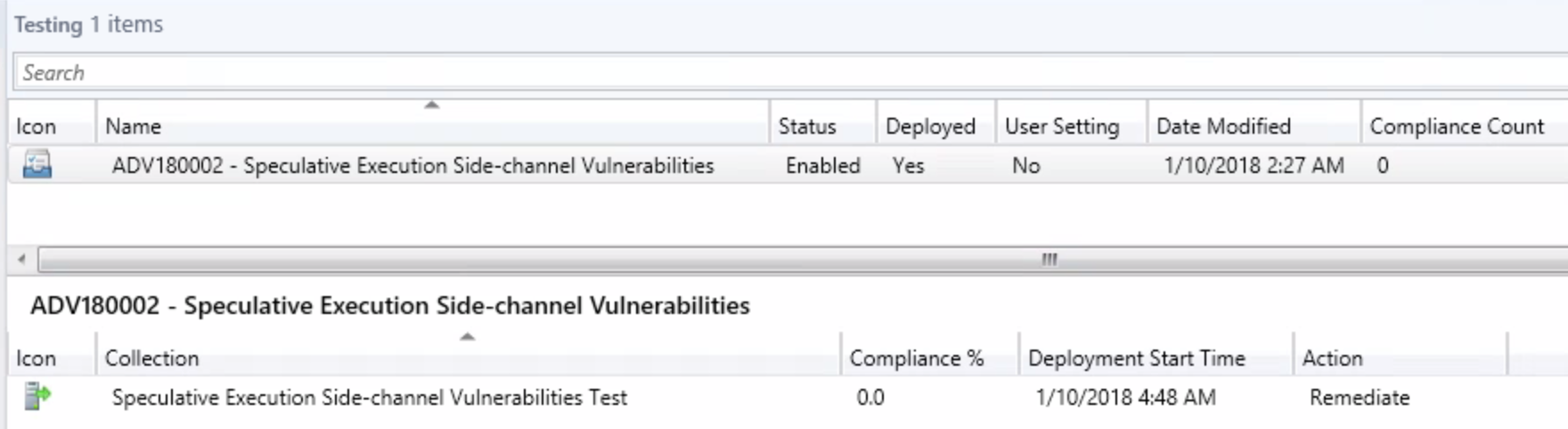
 Step 2 – Package and Deploy the registry keys and Meltdown-Spectre patches via Task Sequence
Step 2 – Package and Deploy the registry keys and Meltdown-Spectre patches via Task Sequence
The first part of the Task Sequence will be a “Check Readiness” to ensure the disk has at least 2GB free space and that there is an eligible OS installed.
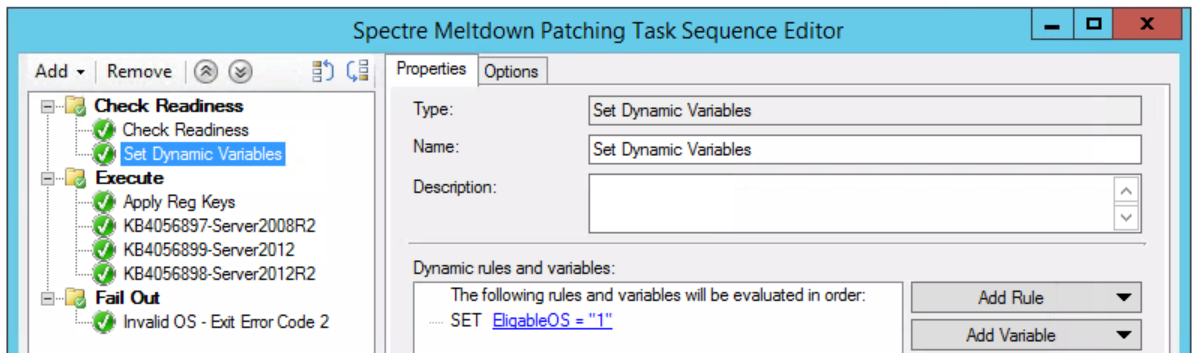 Package the following registry keys and add to the task sequence under the second step, “Execute” (a simple .BAT or .CMD will do just fine):
Package the following registry keys and add to the task sequence under the second step, “Execute” (a simple .BAT or .CMD will do just fine):
reg add “HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerMemory Management” /v FeatureSettingsOverride /t REG_DWORD /d 0 /f
reg add “HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSession ManagerMemory Management” /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
reg add “HKLMSOFTWAREMicrosoftWindows NTCurrentVersionVirtualization” /v MinVmVersionForCpuBasedMitigations /t REG_SZ /d “1.0” /f
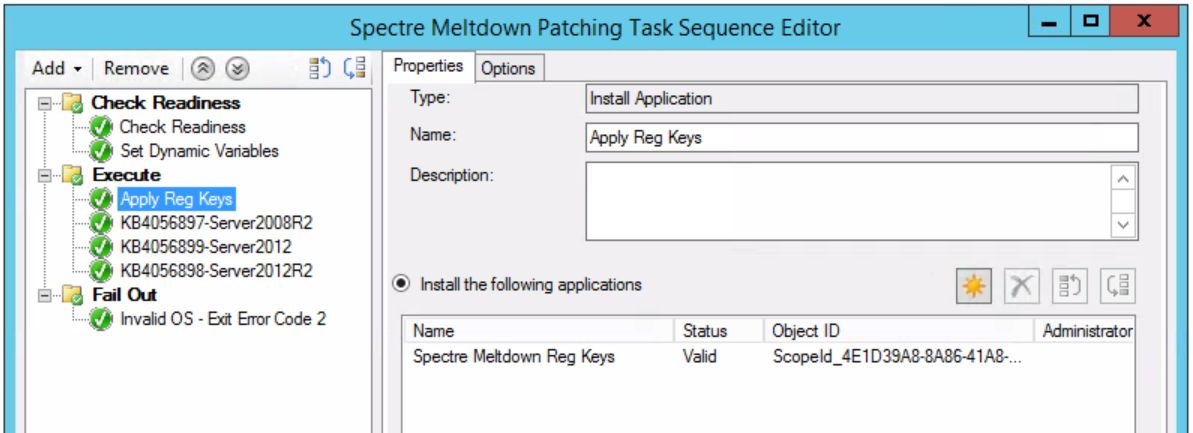 Download and package the following updates and include in the task sequence after “Apply Reg Keys” in the “Execute” portion as shown below:
Download and package the following updates and include in the task sequence after “Apply Reg Keys” in the “Execute” portion as shown below:
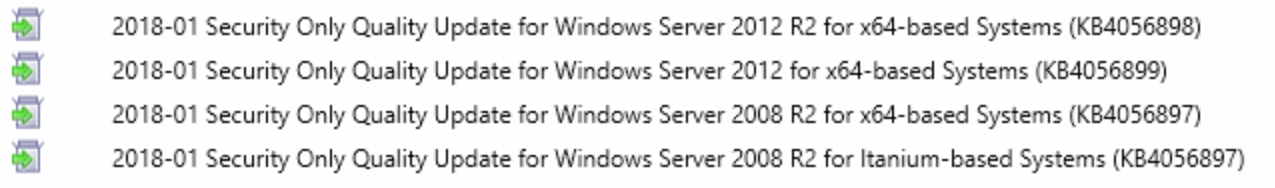
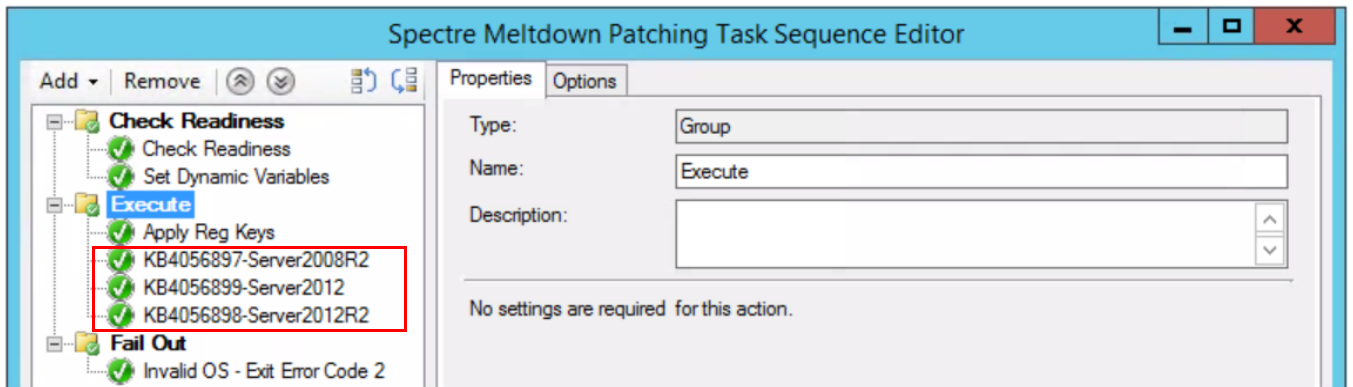 After you’ve deployed everything, head over reporting and look at “Compliance and Settings Management”. Depending on how you want to view compliance, there is an assortment of built in reports that should show you what you want to see.
After you’ve deployed everything, head over reporting and look at “Compliance and Settings Management”. Depending on how you want to view compliance, there is an assortment of built in reports that should show you what you want to see.
 Step 3 – Deploy firmware update (Add to Task Sequence – Optional)
Step 3 – Deploy firmware update (Add to Task Sequence – Optional)
Visit the Firmware vendor list and find the vendor for which you need the firmware for. Once you’ve tested the firmware in your environment, package it up and add that to the task sequence as the last step.
Step 5 – Understanding levels of protection
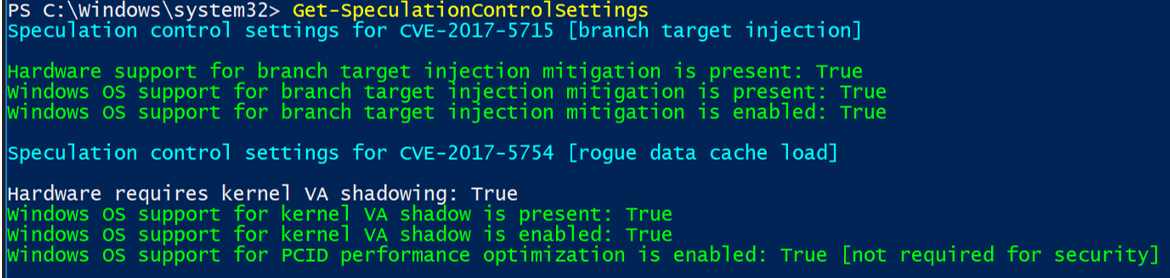
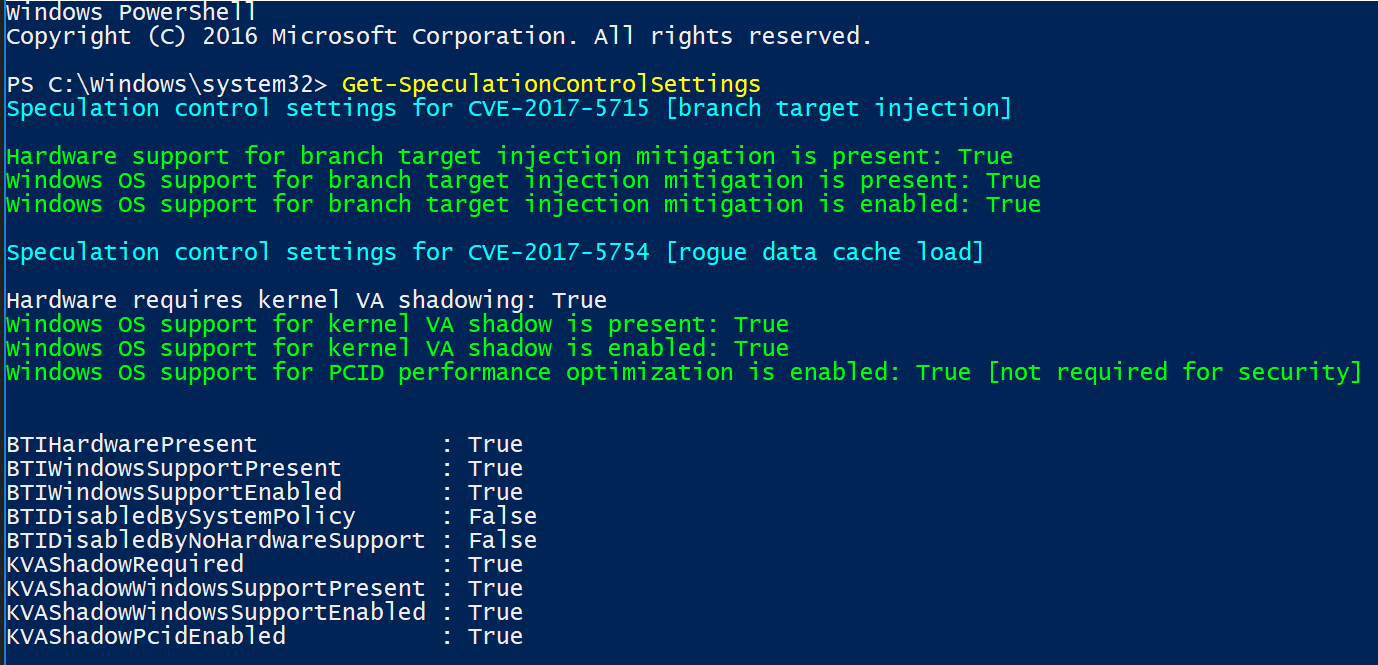 To break this down line by line, I will add the explanation and corelating fix:
To break this down line by line, I will add the explanation and corelating fix:
Hardware support for branch target injection mitigation is present: True (Firmware related)
- Maps to BTIHardwarePresent. This line tells you if hardware features are present to support the branch target injection mitigation. The device OEM is responsible for providing the updated BIOS/firmware that contains the microcode provided by CPU manufacturers. If this line is True, the required hardware features are present. If the line is False (update firmware), the required hardware features are not present, and therefore the branch target injection mitigation cannot be enabled.
Windows OS support for branch target injection mitigation is present: True (January patch related)
- Maps to BTIWindowsSupportPresent. This line tells you if Windows operating system support is present for the branch target injection mitigation. If it is True, the operating system supports enabling the branch target injection mitigation (and therefore has installed the January 2018 update). If it is False, the January 2018 update has not been installed on the system, and the branch target injection mitigation cannot be enabled.
Windows OS support for branch target injection mitigation is enabled: True (OS Registry related)
- Maps to BTIWindowsSupportEnabled. This line tells you if Windows operating system support is enabled for the branch target injection mitigation. If it is True, hardware support and OS support for the branch target injection mitigation is enabled for the device, thus protecting against CVE-2017-5715. If it is False, one of the following conditions is the true:
- Hardware support is not present.
- OS support is not present.
- The mitigation has been disabled by system policy.
Hardware requires kernel VA shadowing: True
- Maps to KVAShadowRequired. This line tells you if the hardware is vulnerable to CVE-2017-5754. If it is True, the hardware is believed to be vulnerable to CVE-2017-5754. If it is False, the hardware is known to not be vulnerable to CVE-2017-5754.
Windows OS support for kernel VA shadow is present: True (January patch related)
- Maps to KVAShadowWindowsSupportPresent. This line tells you if Windows operating system support for the kernel VA shadow feature is present. If it is True, the January 2018 update is installed on the device, and kernel VA shadow is supported. If it is False, the January 2018 update is not installed, and kernel VA shadow support does not exist.
Windows OS support for kernel VA shadow is enabled: True (OS Registry related)
- Maps to KVAShadowWindowsSupportEnabled. This line tells you if the kernel VA shadow feature has been enabled. If it is True, the hardware is believed to be vulnerable to CVE-2017-5754, Windows operating system support is present, and the feature has been enabled. The Kernel VA shadow feature is currently enabled by default on client versions of Windows and is disabled by default on versions of Windows Server. If it is False, either Windows operating system support is not present, or the feature has not been enabled.
Windows OS support for PCID performance optimization is enabled: True [not required for security]
- Maps to KVAShadowPcidEnabled. This line tells you if an additional performance optimization has been enabled for kernel VA shadow. If it is True, kernel VA shadow is enabled, hardware support for PCID is present, and PCID optimization for kernel VA shadow has been enabled. If it is False, either the hardware or the OS may not support PCID. It is not a security weakness for the PCID optimization to not be enabled.
BTIHardwarePresent: True -> apply OEM BIOS/firmware update
BTIWindowsSupportPresent: True -> install January 2018 update
BTIWindowsSupportEnabled: True -> on client, no action required. On server, follow guidance.
BTIDisabledBySystemPolicy: False -> ensure not disabled by policy.
BTIDisabledByNoHardwareSupport: False -> ensure OEM BIOS/firmware update is applied.
KVAShadowRequired: True or False -> no action, it’s a function of the CPU the machine uses
If KVAShadowRequired is TRUE
KVAShadowWindowsSupportPresent: True -> install January 2018 update
KVAShadowWindowsSupportEnabled: True -> on client, no action required. On server, follow guidance.
KVAShadowPcidEnabled: True or False -> no action, it’s a function of the CPU the machine uses
Firmware vendor list:
https://www.intel.com/content/www/us/en/support/articles/000025619/software.html
Guidance to mitigate speculative execution side-channel vulnerabilities – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV180002
Additional guidance to mitigate speculative execution side-channel vulnerabilities – https://blogs.technet.microsoft.com/configurationmgr/2018/01/08/additional-guidance-to-mitigate-speculative-execution-side-channel-vulnerabilities/
Windows Server guidance to protect against speculative execution side-channel vulnerabilities – https://support.microsoft.com/en-us/help/4072698/windows-server-guidance-to-protect-against-the-speculative-execution
The ConfigMgr Speculation Control Baseline – https://gallery.technet.microsoft.com/Speculation-Execution-Side-1483f621
Official Baseline – https://gallery.technet.microsoft.com/Speculation-Execution-Side-1483f621
Deploying Configuration Baselines – https://docs.microsoft.com/en-us/sccm/compliance/deploy-use/deploy-configuration-baselines
Understanding Get-SpeculationControlSettings – https://support.microsoft.com/en-ie/help/4074629/understanding-the-output-of-get-speculationcontrolsettings-powershell