Azure Security Center Playbooks
First off, what is a Playbook in Azure Security Center (ASC)? A Security Playbook is a pre-established and scripted set of actions that can be taken in the event of a specific alert within your Azure tenant (think of System Center Orchestrator Runbooks, but for Azure, aimed towards increased Security for your subscription). Security Playbooks are intended to provide additional security for your cloud resources.
Security Playbooks are built on Azure Logic Apps (https://azure.microsoft.com/en-us/services/logic-apps/). There is a multitude of options within Logic Apps, including built-in templates, and ones you can create blank for security personalization. Keep in mind that due to the fact these are based on another set of technologies within Azure, that means a cost will be associated with each Logic App and triggers (https://azure.microsoft.com/en-us/pricing/details/logic-apps/).
So, this all sounds great, right? You might be wondering what would a real-life example look like for your organization? Here’s a thought: Let’s say Security Center recognizes that on a handful of Azure IaaS resources, have suspicious SVCHOST processes being executed, this is triggered due to the intelligence built into ASC with knowledge that a lot of times Malware tends to use SVCHOST to mask it’s malicious activity. What happens? Alert is triggered, and a Playbook is automatically executed to act on conditions or actions configured by your organization security administrators (e.g. Post a message in Teams, send an Email, run a script, etc.) I bet you want to know how to do this. Here we go:
Creating your first Security Playbook
To create your first Security Playbook, you need to log into the Azure portal and navigate to the Security Center as shown below.
In the Security Center Playbooks are at the bottom of the menu on the left under “Automation & Orchestration.” (this might change upon GA release)
Creating a Playbook is quite simple. All you need to do is click “Add Playbook” button at the top of the interface.
This will take you through a quick wizard, that most of you are now already accustomed to within the Azure Portal. You’ll be asked to name your Playbook, and to put it into a Resource Group (an existing RG or allowing you to create a new RG for this Playbook). Notice you’ll also have the option to turn on Log Analytics, this requires an appropriate workspace to already be previously created for the data to flow into. (optional).
One thing to note, for future automation is that for most resources in Azure (Playbooks included), you’ll have “Automation Options”. This will take you to a JSON editor that shows you the ‘under the hood’ code that you can then pipe into an Azure Resource Manager (ARM) template. Keep this in mind as you expand your Azure footprint.
Configuring a Security Playbook
Once you’ve gone through the wizard to create your Playbook, you’ll see them listed in a manner like below. Keep a close eye on the “Trigger Kind”, we will dig deeper into this later.
Essentially right now you have a blank slate, so let’s dive deeper here. You can start by clicking the name of your Playbook, and it’ll take you into the details of that Playbook (see below).
You will have a plethora of options to choose from when designing your Playbook, I will go into further detail on “Blank Logic App” creation in another document as there are over 290 unique settings, triggers and actions that can be leveraged in your organization if required. One thing to remember, The Logic App Designer is built on a “if this happens, then do that” type of flow (just like Orchestrator from System Center).
When you first launch the Logic App Designer on a new Playbook you are shown the below wizard.
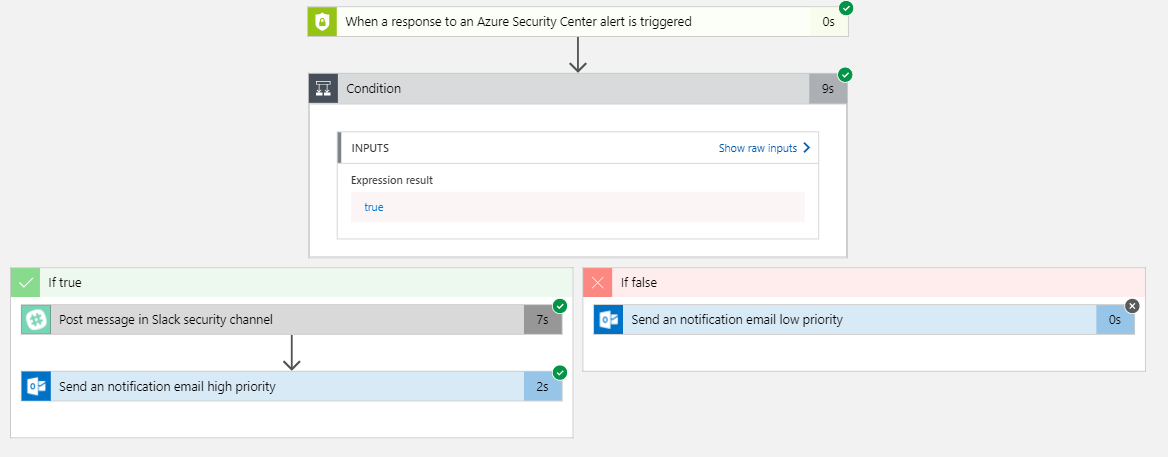
For this example and document, I am going to choose one of the preconfigured templates: “Post message to Teams channel and send email notification”.
The first step before moving on is signing into the services below (in this case Office 365 and Teams). Once you successfully sign in and allow permissions for this Playbook, you’ll be able to continue.
In this basic example, the Playbook template will send a recipient a notification when Security Center Alerts are generated. It’ll (based on your configuration) send an email for low priority alerts, and for high priority alerts notify the Teams site. All of the settings mentioned are configurable to your organization testing standards as needed.
In case you’re curious on how many potential actions are available in Playbooks, I scrolled down and selected “Add a step” and choose an “Add an action”. This gave me a chooser with 290 separate actions I can add to this Playbook.
As a next step, begin testing and working with Playbooks. Sometimes it’ll take a bit to firmly grasp the amazing opportunities and automation this presents your organization, but I implore you to dig deep! If you’d like some templates / starter kits, I’ve provided some links below!
Helpful Starting Points (Playbook Starter Kits):
Virus attack playbook – https://aka.ms/ASCPlaybooksVAttack – deploys 2 virtual machines, OMS and associated network resources. One of the VM is deployed without endpoint protection
SQL Injection playbook – https://aka.ms/ASCPlaybooksSQLi – deploys 2 application gateway, a web app and SQL server and database and OMS
XSS (cross site scripting) attack – https://aka.ms/ASCPlaybooksXSS – deploys 2 application gateway, a web app and SQL server and database and OMS
DDoS protection – https://aka.ms/ASCPlaybooksDDos – deploys a virtual machine an associated network resources (including public IP address) and OMS
Additional Links: